TL;DR – if you’re having issues with the user profiles not saving your settings, ignore the primary driver profile. Steps to fix.
I’ve been reading a lot of posts on Reddit and vwidtalk forums about the user profiles and how it doesn’t seem to work. I’ve not come across a post though that proposes a solution. This is what I did to finally get all the settings to work with profiles: ignore the primary driver profile.
We purchased our ID.4 at the end of July. This is Noelle’s vehicle and as such, I added her as the primary driver, and me as a secondary. She’s had non-stop issues with the seat not going back to where she wants it, or it’ll suddenly reset her ambient light settings, switch her driving mode to something else, etc. Initially, she blamed me for changing her settings and not putting them back (I take the ID.4 to shuttle kids to before-school activities, or quick errands when she isn’t using it), but then she experienced the same thing when getting into the car after work.
Oddly enough, during this whole time, my profile seemed to work just fine. When I switched to my profile, it would move my seat to the correct position. Switching to her profile, it would say it was moving the seat, but never actually did. My profile would switch back to the last driving mode I used, the last ambient light setting, etc. but switching to her profile was a roll of the dice to see what you got.
The final straw was the car locked her out of her profile because she hadn’t logged in recently into the app. WTF? Why should she need to log into the app at all? It prompted her for an “S-PIN” and when she couldn’t remember it, it completely locked her out and she could only use the guest profile. At this point, I decided to factory reset the infotainment center and start over from the beginning.
I reset the infotainment center and went down the path of re-adding her as the primary driver, but now the Infotainment center informed me that it was loading her settings and any changes I make would not be saved. I went ahead and moved forward with setting up my profile. I came back later to her profile and it continued to state it was syncing her account, changes would be lost, etc. Sure enough, if I made a change to her profile (e.g. Ambient lighting colors), switched to another profile, and then back, the changes were lost. This continued for two hours. I assumed something had to be wrong, so I reset the Infotainment center again.
This time though, I decided to just reset everything to zero. So not only did I factory reset the Infotainment Center, but I also deleted her account from the myVW app, as well as my account. I decided this time around to make a fake “primary” driver account, and then add her real account as a secondary driver, and it worked! Now when we switch profiles between her real profile and my profile, the car switches correctly!
Here is the complete list of steps I took:
Steps
- Reset the Infotainment Console to remove all previous profiles
- Remove all accounts from the myVW app
- Create a new account in the myVW app
- Add the primary driver account in the ID.4, following the steps in the Infotainment Console. We are going to completely ignore this profile later
- Create a new account via https://carnet.vw.com/ to use for the actual primary driver, NOT in the myVW app. This will require a second email address and a second phone number.
- If you’re using gmail, you can use the `+` trick for creating a vanity email address. If your email address is [email protected], add a `+` and whatever after the account name. I.e. [email protected]. We have to use carnet.vw.com to create the account because the myVW app flags the email address as invalid.
- The myVW app requires a phone number it can text message but carnet does not. I used a Google Voice number for this step.
- In the myVW app, while still logged in as the user we created in step 3, add an authorized user to the vehicle and use the same email address from step 5
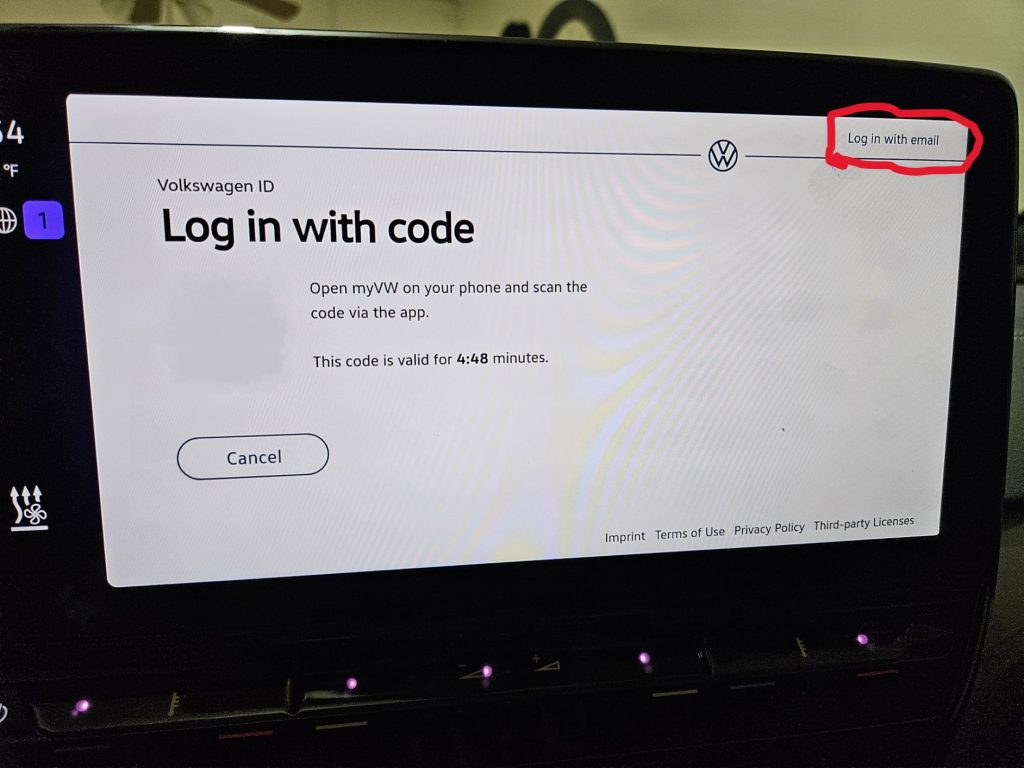
- In the vehicle, add a new user profile, but DO NOT USE THE QR CODE! Instead, click on the “Login with email” section in the upper right corner (see photo below)
- Log into the profile with the email address and password you set up in step 5. This is now your REAL primary driver profile
- Make sure you are in the profile, and make adjustments to the vehicle as you need (e.g. seat position, ambient lighting, driving mode, etc)
- Get out of the vehicle
- Lock the vehicle
- Unlock the vehicle
- Get in the vehicle
- Press the brake pedal to start the car
- Repeat steps 5-14 to add and save a secondary driver profile, though now you can use a real email address and phone number for all other users
Now when we switch user profiles EVERYTHING works like we expect it to: the seat and mirrors move into the correct position, the ambient lighting changes to the colors and brightness as set, the vehicle switches to the last driving mode the user set, etc. We’ll see if it continues to work but so far, it’s still working.






